Web Platform
A Modern Platform for Threat Mitigation & Ethical Hacking
We’ve created a platform that makes threat mitigation and ethical hacking available for everyone, regardless of their technical background.
Introducing XAHICO Web Platform ~
Overview
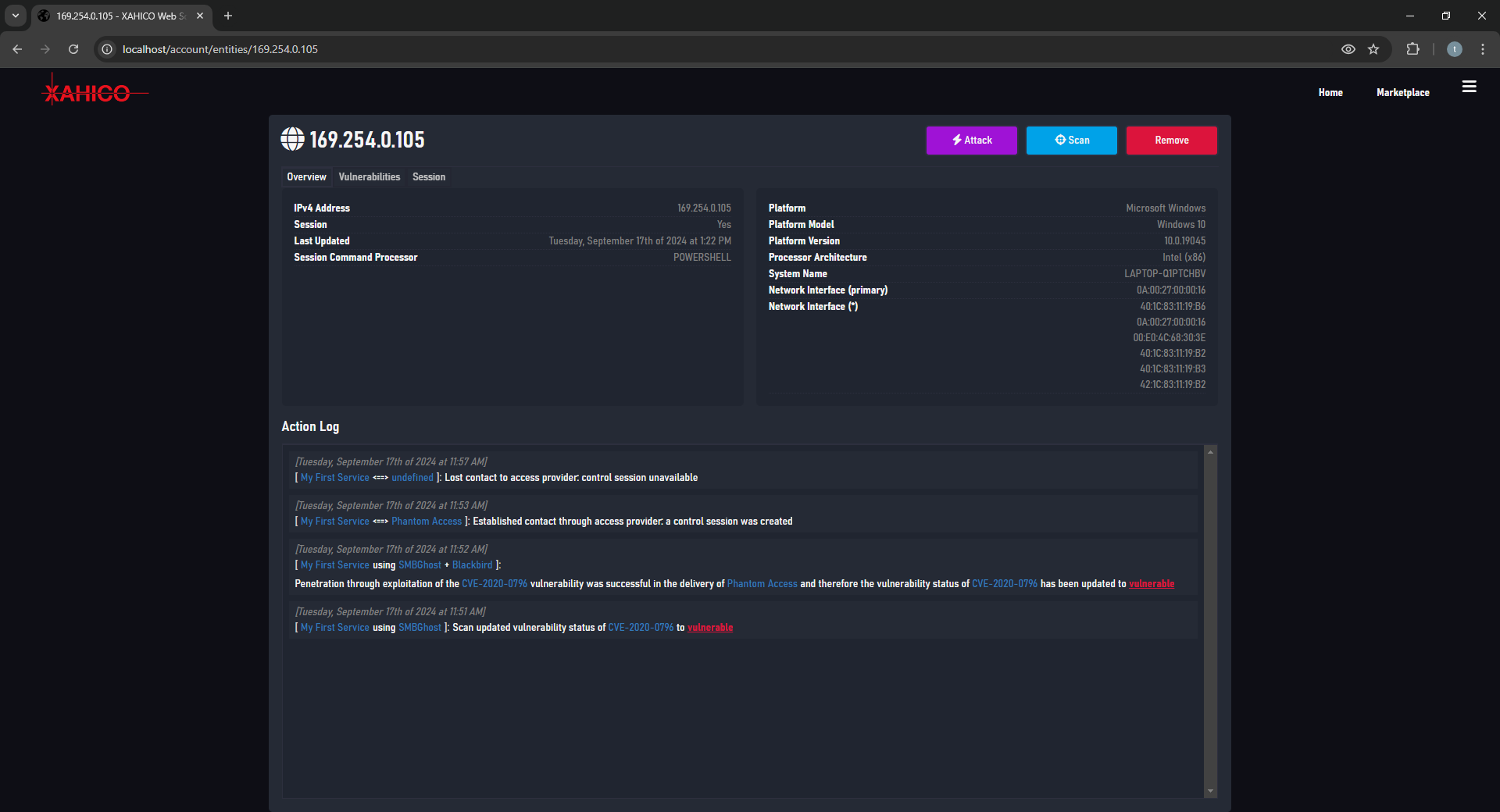
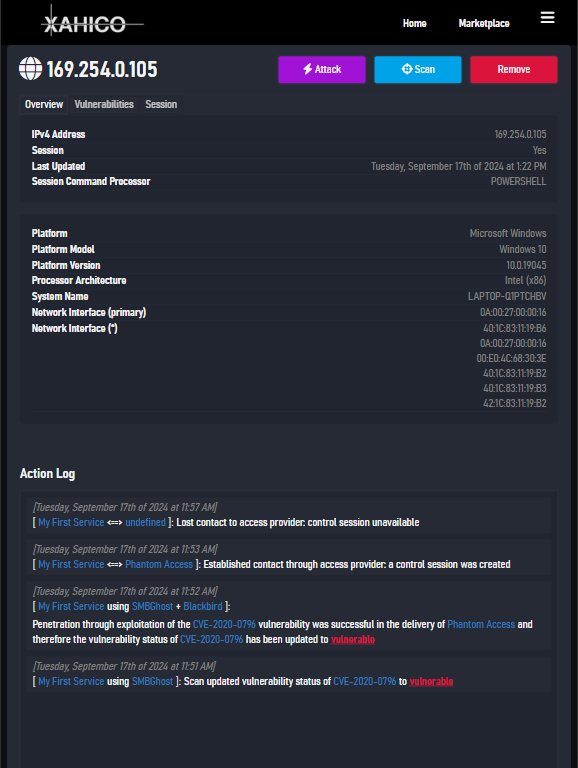
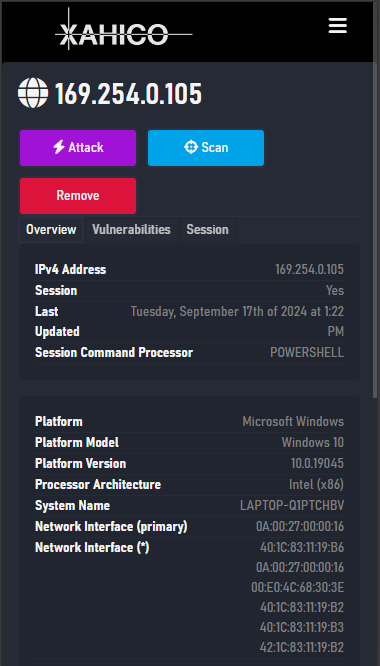
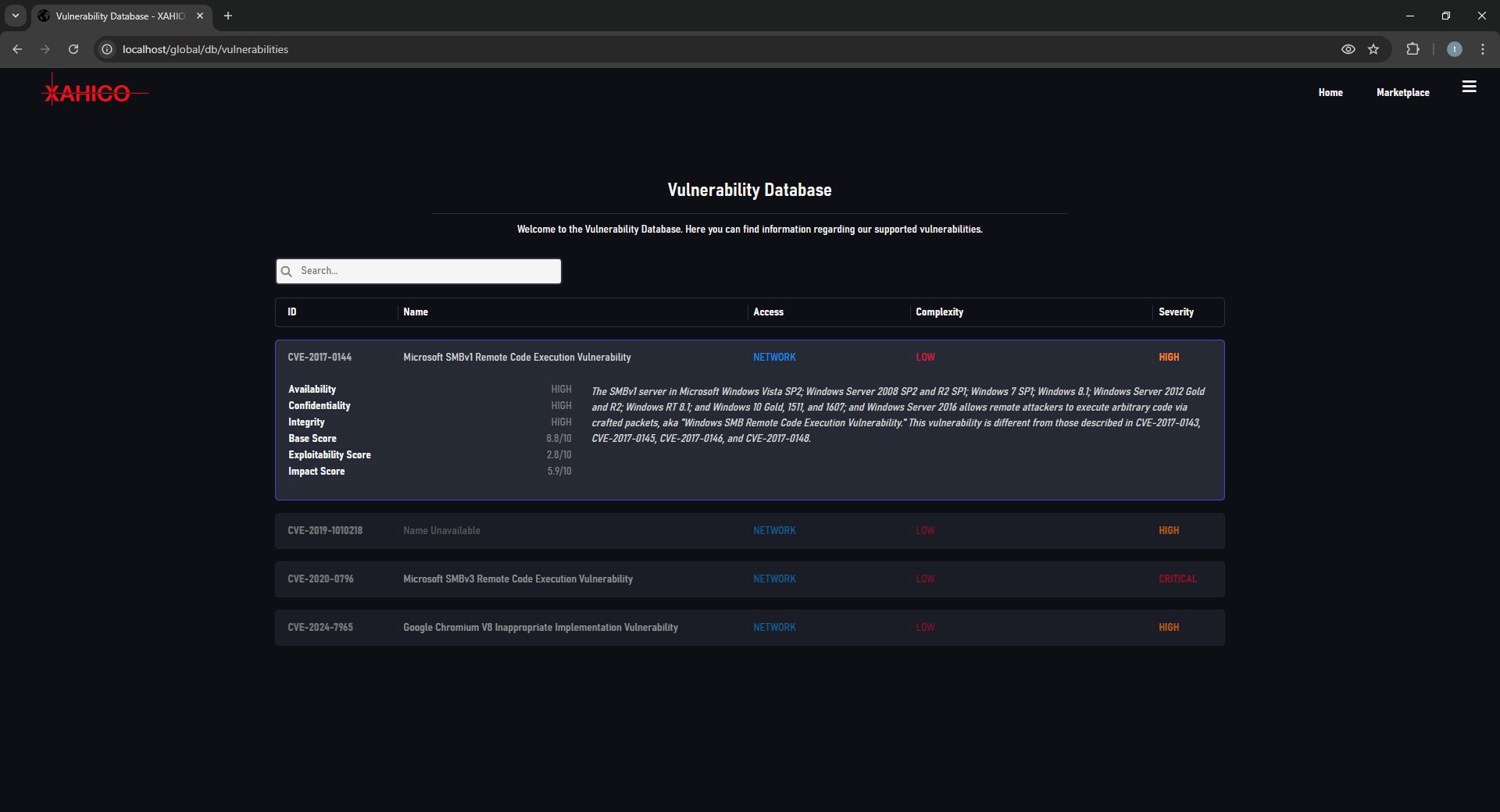
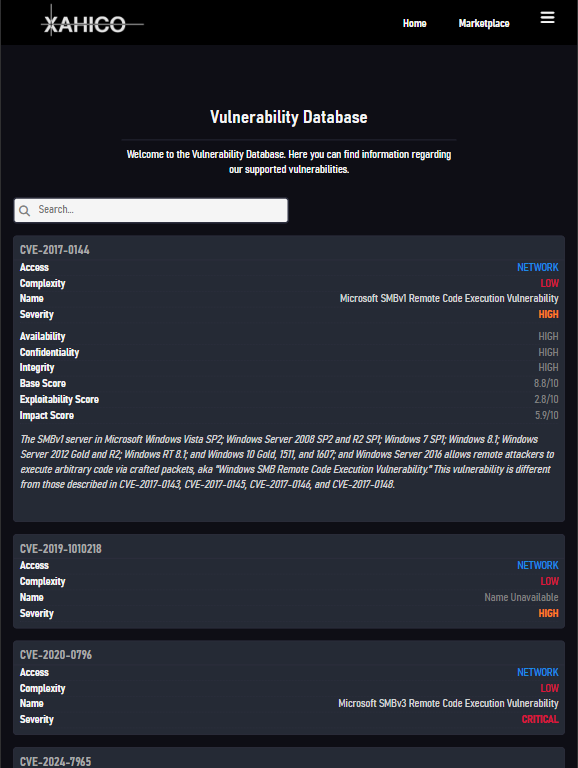
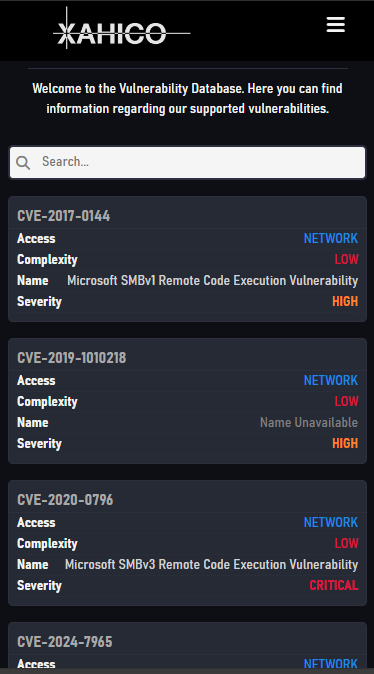
The XAHICO Web Platform is a digital ecosystem with a vast infrastructure and various powerful toolchains, systems and services for vulnerability detection, penetration testing and adversary simulation.
For Businesses & Individuals
The Web Platform may also be used to conduct controlled cyber-attack simulations without actual threat, using our government-grade penetration testing tools, to
- Promote secure practices within workplaces
- Assess how employees and systems would react in a real attack scenario
- Get a much wider and more accurate view of the exposed systems' attack surface to truly minimize future threats
For Penetration Testing Service Providers
For Everyone
Why We Exist
Our goal is to address the challenges of conducting
cybersecurity operations by offering an all-in-one
tool that is designed to make cybersecurity
accessible, efficient, and simple.
Despite the virtualization of technologies as of late,
current cybersecurity solutions have not fully embraced
the capabilities of the 21st century,
and to properly conduct cybersecurity operations involves
juggling a lackluster of different tools,
each with their varying dependencies, licenses, syntaxes,
and user manuals.
We’ve created an intelligent solution to streamline this
complexity.
Our whole platform is virtual, so there are no downloads,
and it is accessible anywhere, anytime via any internet
browser (supported on Google Chrome, Microsoft Edge, Opera and latest Mozilla Firefox),
on desktop and mobile devices.
Our platform supports both the analysis and ingression of targets,
in addition to the sustained control of systems through
leveraging platform-specific persistence methods,
a feature which itself allows for unparalleled adversary simulation.
Our motivation to create a platform for everyone to share stems
from the fact that there exists a prevailing notion that security
measures should be exclusively managed by degreed professionals
with certificates, using tools often carrying annual fees of
$6,000 to $50,000.
This exclusivity, both professionally and financially, serves as a
significant barrier to entry. We advocate for a perspective that
positions cybersecurity to be as accessible as any other professional
or personal pursuit.
With the increasing trend of miscellaneous threat factors and
Advanced Persistent Threats, safeguarding of servers and smart devices
has become imperative for businesses and individuals alike.
Nonetheless, protecting these assets can be a costly, time-consuming
and frequently neglected endeavor, particularly for small businesses
and individuals.
Small businesses may opt to just roll the dice with their security due to the expenses associated with implementing comprehensive security measures, while individuals often refrain from engaging in such endeavors due to the barriers to entry and associated costs.
We are looking to establish a lasting place in this industry as a cornerstone everyone can afford and rely on.
Why Choose Us
There are critical aspects to take into consideration when choosing your security provider, and we would like to outline how we compare to competition in the following areas:
Considerations
- Cost: Businesses interested in having their systems audited by a penetration testing services company are faced with a price tag often in the range of $5,000 to over $100,000 — for one audit. Using our platform you can audit your systems daily for the comparatively insignificant recurring monthly fee of your service (see our Pricing)
- Efficiency: Our platform is the only software in the 'known world' capable of executing the full kill-chain — a feat otherwise requiring at minimum 3 rival software, each independently carrying a higher price tag than ours
- Ease-of-use: Our platform is inarguably the easiest to use cybersecurity tool in the world, as it is designed for a much wider audience than existing solutions and not littered with industry-specific acronyms and buzzword terminology
- Scalability: Scalability and modularity have been core aspects that were taken into consideration in the development of the platform. We have taken great expense in ensuring that our platform carries as few limitations as possible, and can handle anything from operations on single targets to targets in the billions
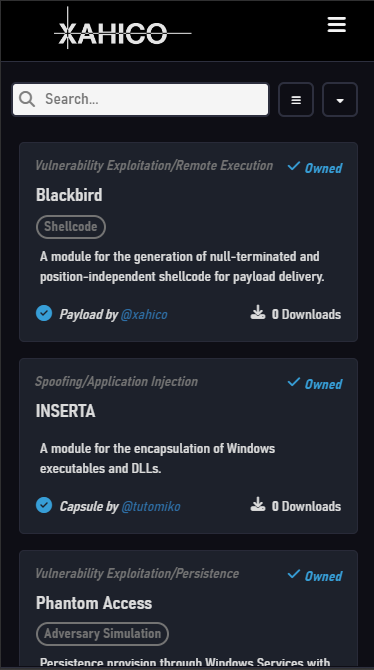
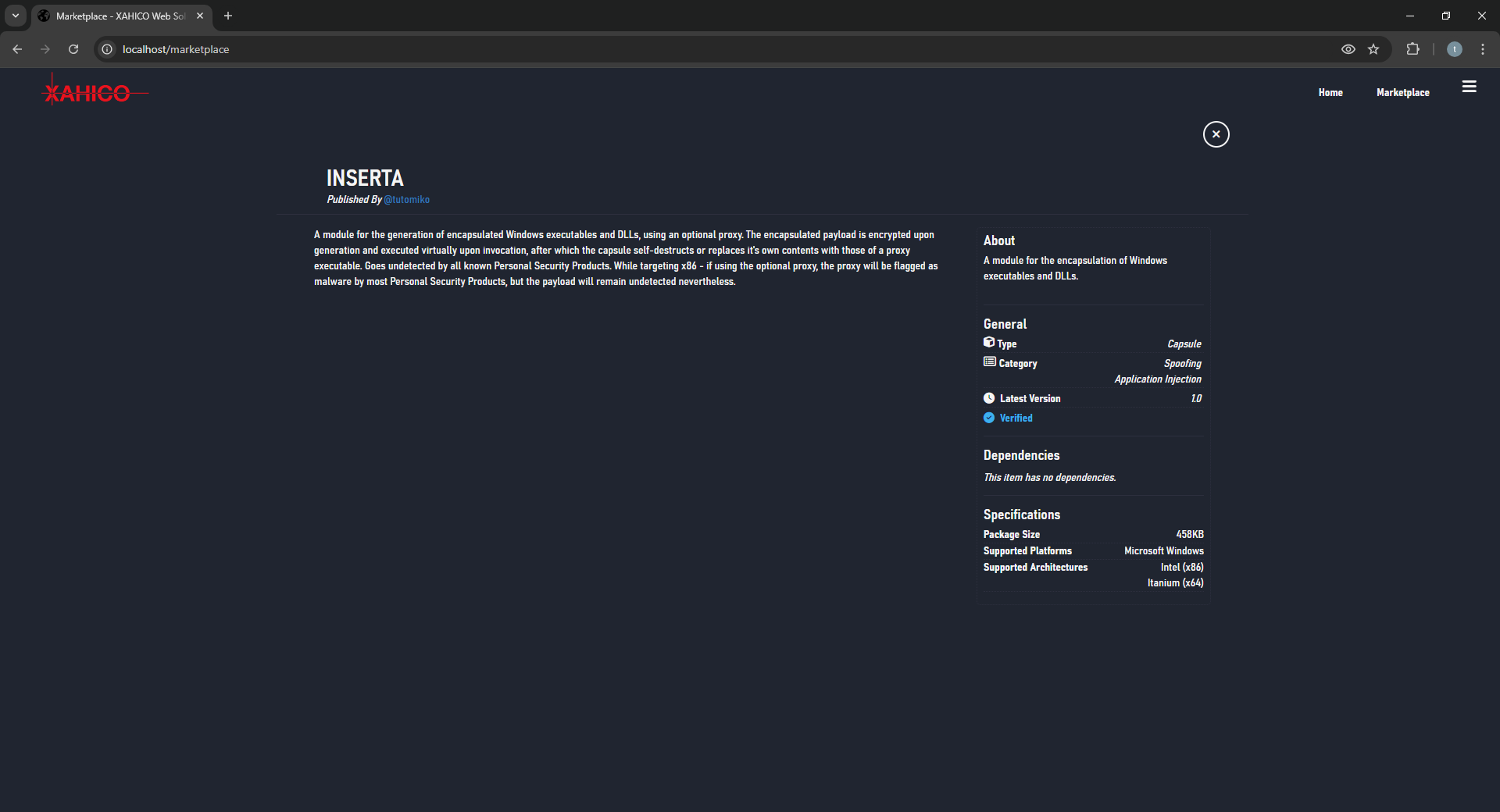
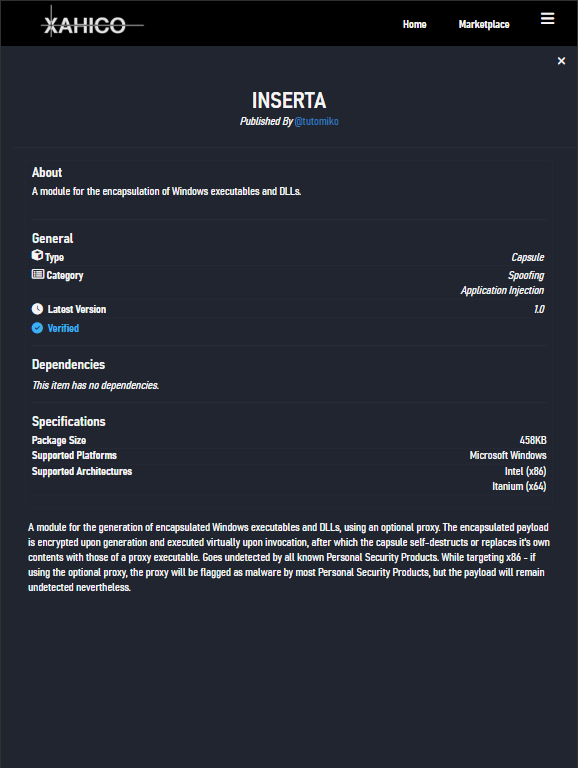
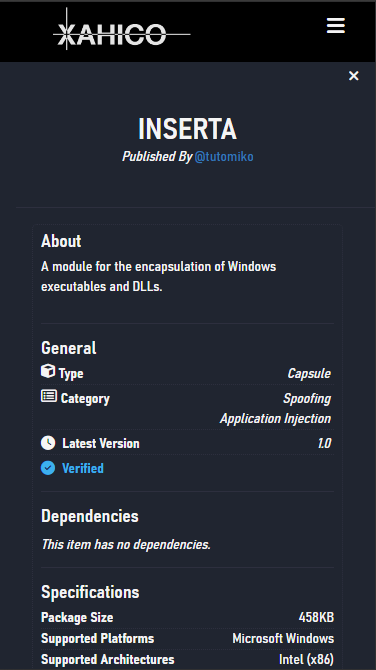
Key Features
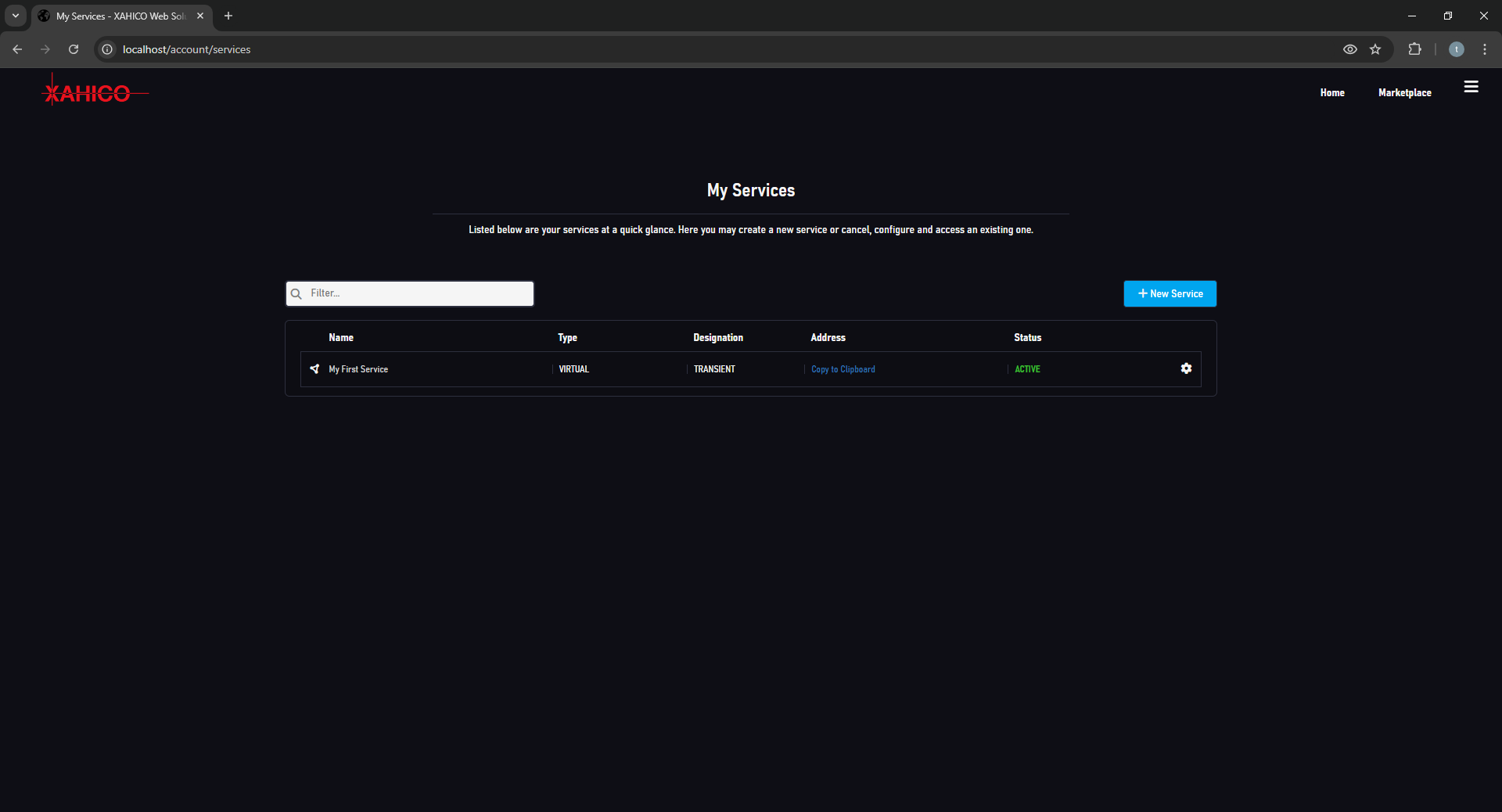
- Fully cloud-based (SaaS) without downloads required
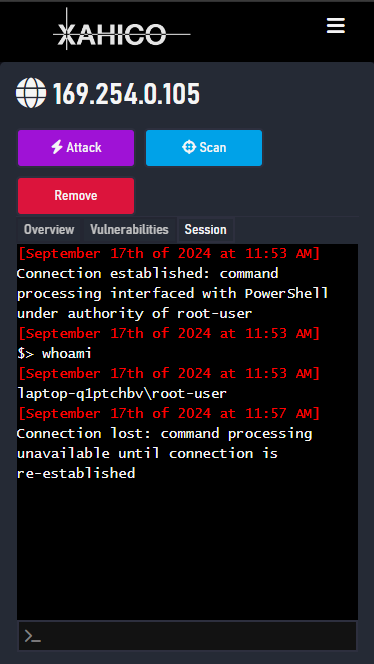
- Capable of handling the whole kill-chain: supports vulnerability detection, exploitation and adversary simulation through Command & Control sessions
- No false positives, with 100% accuracy using proof-based verification (not "six sigma," which is about 50-50) -- additionally, all gathered information is given a reliability rating depending on the information's source and the gatherer's reliability
- Modern user interface with simplistic and user-friendly design
- Supported on any major browser on any operating system
- Lightweight and designed for compatibility and excellent user-experience on desktop, phone or tablet
- Most beginner-friendly on the market -- Absolutely no background in cybersecurity or its principles required
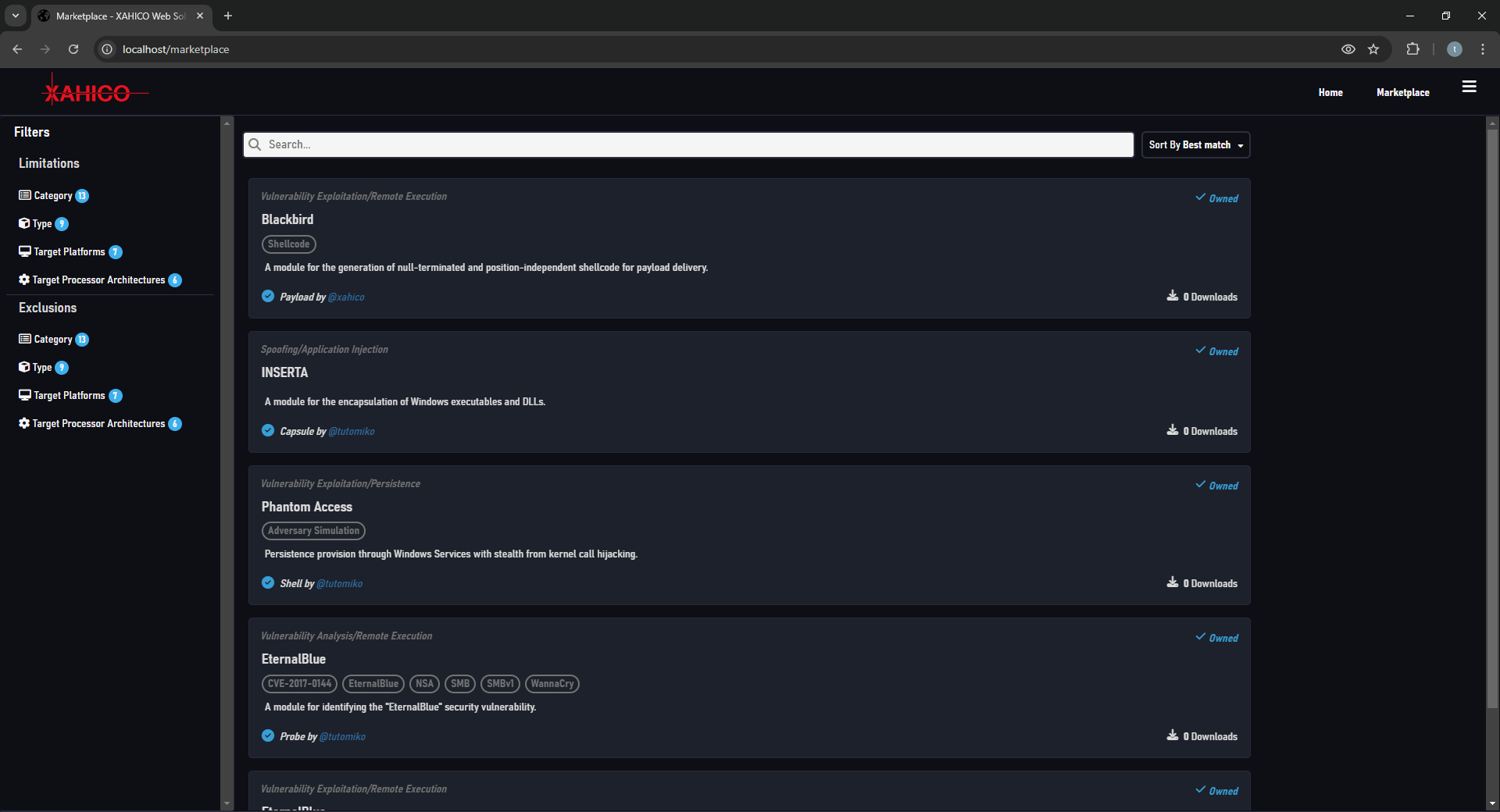
- Modular with fully configurable modules
- Supports user-created modules within the service's own Marketplace
- Control Sessions support Windows and Linux targets -- support for Mac/OSX, Android and BSD planned
- Re-usable test / attack parameters for rapid deployment, also shareable with other users
- Multithreaded operations over virtually unlimited targets (limited to 263-1 x 263-1 targets in total per task) using Balanced Load Fragmentation
Technical Details
Roadmap 2024
We've outlined our strategy for 2024,
marking our entry into the cybersecurity industry.
What's planned for 2024?
- Initial funding round on Indiegogo.com with campaign set to launch on October
- Service beta launch on November
- Module Studio -- a graphical user interface for the development of modules (currently being actively developed) to be released on December
- Grouped Control Sessions -- Command & Control over networks of entities, scheduled for late December of 2024
Contribute
Contributions are the heart of the cybersecurity industry,
and greatest innovations in tech can be sourced to
leisure time creations by hobbyists.
We see an immeasurable collection of Proof-of-Concept (PoC)
work on GitHub for vulnerability detection and exploitation,
published by individuals to highlight these dangers,
bring attention to them and help remediate them.
Most cybersecurity companies do not care about the fact that
they wouldn't thrive without these individuals
so they take them and their work for granted,
but we understand the importance and greatly value
these efforts and the people behind them.
We want you to be a part of our community.
We wish to build a community based on sharing and open
communication,
where each individual has a voice that matters.
As we value our community and wish to show our dedication,
we listen to our community in many ways.
In addition to welcoming suggestions on changes to the
platform, we've implemented
Community Polls.
What are Community Polls?
This means that no major update is pushed unless at least 51% of the community agrees on it.
Due to the cloud-based design of the platform,
we are unfortunately unable to offer the service entirely
free of charge.
However, we are dedicated to ensuring the accessibility
of the service for all.
That's why we've created the
Community Points & Contributor Reward System.
What are Community Points?
It is our way of rewarding contributions and show our appreciation to the community.
What is the Contributor Reward System?
- Users are rewarded for reporting bugs and receive Community Points for reported bugs at an amount based on the severity of the bug
-
Users are rewarded Community Points for the creation of modules,
and will receive Community Points initially upon publishing in
addition to the continued success of their modules,
measured in the modules' popularity.
The rewarded amount is based on the complexity, consistency, reliability,
usefulness, and type of the module.
It should be noted that this only applies to modules that are published as 'free of charge.' - Users are rewarded Community Points for sharing the platform on social media, or for in other ways helping us grow.
Pricing
Are you tired of having to contact a sales representative
for basic pricing information,
then being sold a ton of features you didn't need for a small
fortune?
At XAHICO
we believe you should only pay for what you need.
That's how we're able to sell our service for a fraction of
the cost of competitors.
Let's make it simple
- Pricing for services start at $62.00/mo, however they are fully customizable and can range upto ~$5000.00/mo for medium-large businesses with higher demands and specialized needs
- In addition to the vast and growing selection of free modules, we offer a selection of more advanced modules at reasonable prices, often in the range of $20.00 - $100.00 per module, depending on their complexity. Some modules require constant development and are sold on a subscription basis, with a price in the range of $10.00 - $50.00 per month
Why/how is our price so low compared to competition?
Through leveraging modern technologies and smart designs, we've managed to create a very cost-effective yet powerful solution. With low operational costs we are able to maintain the lowest price on the market.
About Us
XAHICO is a finnish cybersecurity
startup founded in mid-2024.
Foundation for the Web Platform
began development in 2020 by a founding member of XAHICO,
Tuomas Kontiainen,
inspired by the lack of available products that could deliver
without a 5-digit price tag and a user manual comparable in complexity
and page count to a Dostojevski classic.
The platform was developed without any external dependencies
to ensure full control over performance, availability and easy
maintainability of the Web Platform codebase.
Stability testing of the platform began in early 2024,
with the platform reaching version 1.0 (beta) on
September of 2024.
Key People Behind This Project
- Tuomas Kontiainen, Founding Member & Lead Developer, Cybersecurity Specialist
- Niina Kampman, Founding Member
Contact Us
Contributors may contact us
through our social media channels.
For business inquiries, you may contact us at
contact.enterprise@xahico.com